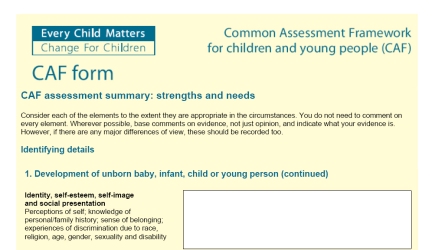
A company called Cryo-cell International Inc. has launched its proprietary cryopreservation service, C’elle, which offers women the opportunity to bank stem cells from their menstrual blood. Using a menstrual cup to collect their blood is at the same time offering some vague belief that in the future you might be able to be saved by the possible stem cells collected from it. This company has already been under criticism from scienctists deeming the process to be all ‘hypothesis and hype’.
A caption taken from the C’elle promotional website:
“When it comes to making major life decisions, there is no time like the present. And when it comes to something as important as collecting potentially life-saving stem cells found naturally in menstrual blood, the ideal time is NOW. Thanks to C’elle’s patented technology, and easy-to-use collection kit, you have the reassurance and peace of mind you need, when it comes to collecting, isolating and preserving menstrual blood. Welcome to C’elle – where every month holds a miracle. ”
Read more about C’elle at BBC news and Bionews>
The Museum of Menstruation is unfortunately closed down but check out what the owner has to say about menstruation knickers and his menstrual cup ball gown.
Filed under: stemcells | Tagged: future, health, product, protection | 1 Comment »